This article is for Windows users who want to create and use secure shell (SSH) keys to connect to Linux virtual machines (VMs) in Azure. You can also generate and store SSH keys in the Azure portal to use when creating VMs in the portal.
To use SSH keys from a Linux or macOS client, see the quick steps. For a more detailed overview of SSH, see Detailed steps: Create and manage SSH keys for authentication to a Linux VM in Azure.
Overview of SSH and keys
SSH is an encrypted connection protocol that allows secure sign-ins over unsecured connections. SSH is the default connection protocol for Linux VMs hosted in Azure. Although SSH itself provides an encrypted connection, using passwords with SSH still leaves the VM vulnerable to brute-force attacks. We recommend connecting to a VM over SSH using a public-private key pair, also known as SSH keys.
SSH stands for Secure Shell and is a cryptographic protocol based on the concept of public-private keys. We are using SSH with Git because it is much easier than typing your username and password. When adding your SSH key to the agent, use the default macOS ssh-add command, and not an application installed by macports, homebrew, or some other. SSH Keys and Public Key Authentication. The SSH protocol uses public key cryptography for. Use SSH keys for authentication when you are connecting to your server, or even between your servers. They can greatly simplify and increase the security of your login process. When keys are implemented correctly they provide a secure, fast, and easy way of accessing your cloud server.

The public-private key pair is like the lock on your front door. The lock is exposed to the public, anyone with the right key can open the door. The key is private, and only given to people you trust because it can be used to unlock the door.
The public key is placed on your Linux VM when you create the VM.
The private key remains on your local system. Protect this private key. Do not share it.
When you connect to your Linux VM, the VM tests the SSH client to make sure it has the correct private key. If the client has the private key, it's granted access to the VM.
Depending on your organization's security policies, you can reuse a single key pair to access multiple Azure VMs and services. You do not need a separate pair of keys for each VM.
Your public key can be shared with anyone, but only you (or your local security infrastructure) should have access to your private key.
Supported SSH key formats
Azure currently supports SSH protocol 2 (SSH-2) RSA public-private key pairs with a minimum length of 2048 bits. Other key formats such as ED25519 and ECDSA are not supported.
SSH clients
Recent versions of Windows 10 include OpenSSH client commands to create and use SSH keys and make SSH connections from PowerShell or a command prompt. This is the easiest way to create an SSH connection to your Linux VM, from a Windows computer.
You can also use Bash in the Azure Cloud Shell to connect to your VM. You can use Cloud Shell in a web browser, from the Azure portal, or as a terminal in Visual Studio Code using the Azure Account extension.
You can also install the Windows Subsystem for Linux to connect to your VM over SSH and use other native Linux tools within a Bash shell.
Create an SSH key pair
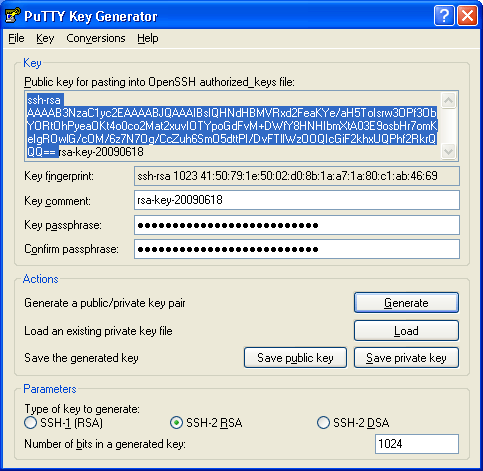
Create an SSH key pair using the ssh-keygen command. Enter a filename, or use the default shown in parenthesis (for example C:Usersusername/.ssh/id_rsa). Enter a passphrase for the file, or leave the passphrase blank if you do not want to use a passphrase.
Create a VM using your key
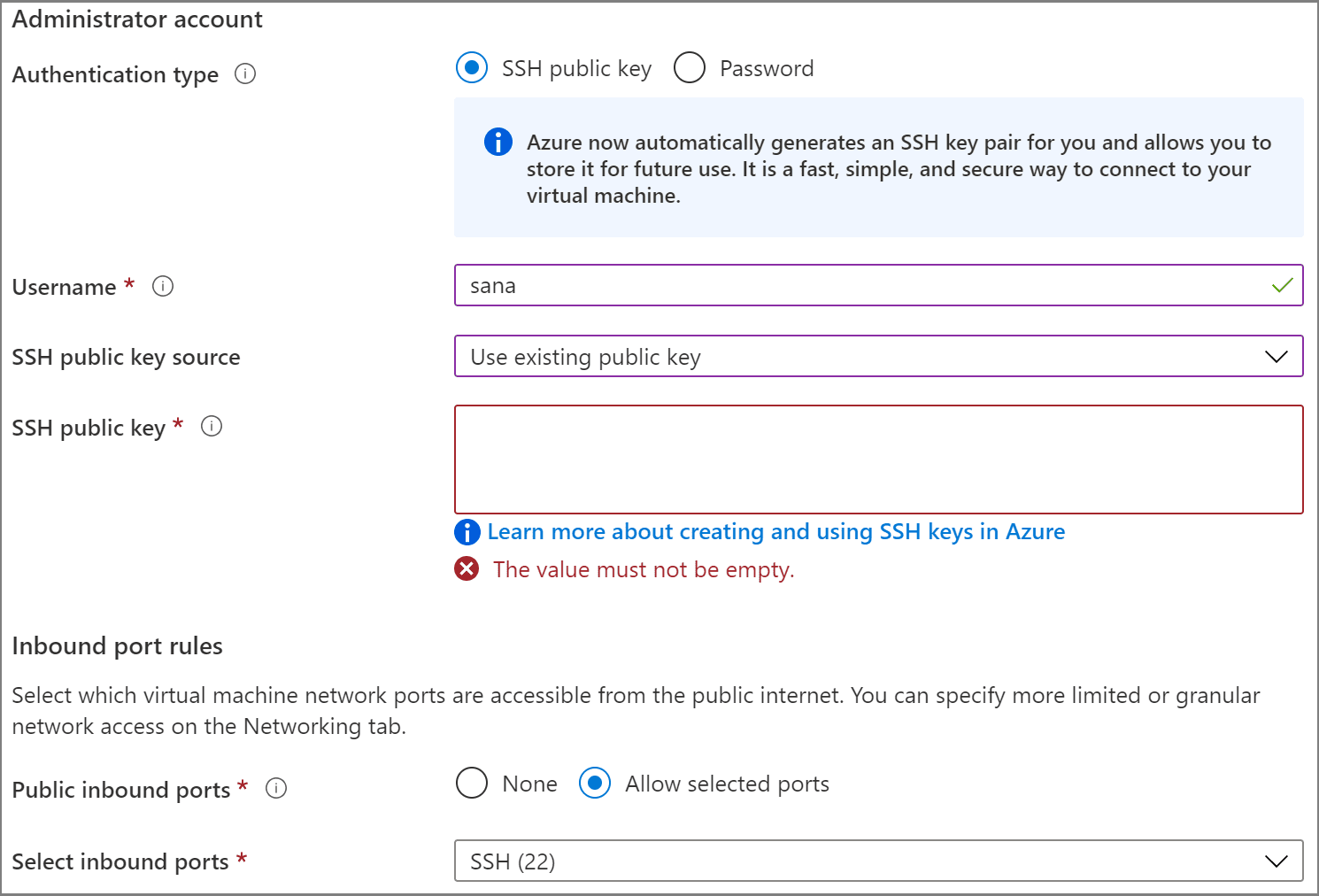
To create a Linux VM that uses SSH keys for authentication, provide your SSH public key when creating the VM.
Using the Azure CLI, you specify the path and filename for the public key using az vm create and the --ssh-key-value parameter.
Ssh Keys Download
With PowerShell, use New-AzVM and add the SSH key to the VM configuration using`. For an example, see Quickstart: Create a Linux virtual machine in Azure with PowerShell.
If you do a lot of deployments using the portal, you might want to upload your public key to Azure, where it can be easily selected when creating a VM from the portal. For more information, see Upload an SSH key.
Connect to your VM
With the public key deployed on your Azure VM, and the private key on your local system, SSH to your VM using the IP address or DNS name of your VM. Replace azureuser and 10.111.12.123 in the following command with the administrator user name, the IP address (or fully qualified domain name), and the path to your private key:
If you configured a passphrase when you created your key pair, enter the passphrase when prompted.
If the VM is using the just-in-time access policy, you need to request access before you can connect to the VM. For more information about the just-in-time policy, see Manage virtual machine access using the just in time policy.
Ssh Key File
Next steps
For information about SSH keys in the Azure portal, see Generate and store SSH keys in the Azure portal to use when creating VMs in the portal.
For detailed steps, options, and advanced examples of working with SSH keys, see Detailed steps to create SSH key pairs.
You can also use PowerShell in Azure Cloud Shell to generate SSH keys and make SSH connections to Linux VMs. See the PowerShell quickstart.
If you have difficulty using SSH to connect to your Linux VMs, see Troubleshoot SSH connections to an Azure Linux VM.

У меня есть две машины с одинаковыми .ssh/authorized_keys (проверено, поскольку (1) одна является копией другой и (2) совпадают md5sums файла на обеих машинах)
и тот же /etc /ssh /sshd_config (проверено, поскольку (1) один является копией другого и (2) совпадают с md5sums).
SSHD был перезапущен на обеих машинах.
Один работает (используя метод publickey, т.е. Я могу войти без ввода пароля), а другой нет.
Запуск ssh -vv показывает следующее:
Хорошая машина отображает:
Плохая машина отображает:
Какие-нибудь мысли?
Ssh Ssh Key Only
Смотрите комментарии: «Изменение .ssh на 700 и авторизованных ключей на 600 сработало. Но почему это работает на «хорошей машине»?'
Ssh Ssh-keyscan
Всё ещё ищете ответ? Посмотрите другие вопросы с метками sshssh-keysopenssh.
